Cyberattacks carry more risk in today's digital world than they did years ago. Small or big companies alike have to be ready for security breaches. Having a strong incident response plan in place will help lessen the effects of cyber hazards. Here is where knowledge of the seven phases of incident response becomes essential.
The incident response lifecycle guides companies toward systematic security breaches. By working with the best incident response companies or using dependable incident response services, businesses can minimize damage, shorten recovery times, and protect their brand.
Let us examine the main stages of the incident response lifecycle and see how your company may gain from expert incident management consultancy and cyber security incident response services.
What Is an Incident Response?
Incident response involves the identification, control, and minimization of security events. To manage breaches correctly, specialist incident response software, incident response management software, and trained incident response teams must be adopted.
Businesses that invest in expert incident response services are better suited to managing online risks. Leading incident response companies offer complete security response services to reduce the effects of breaches.
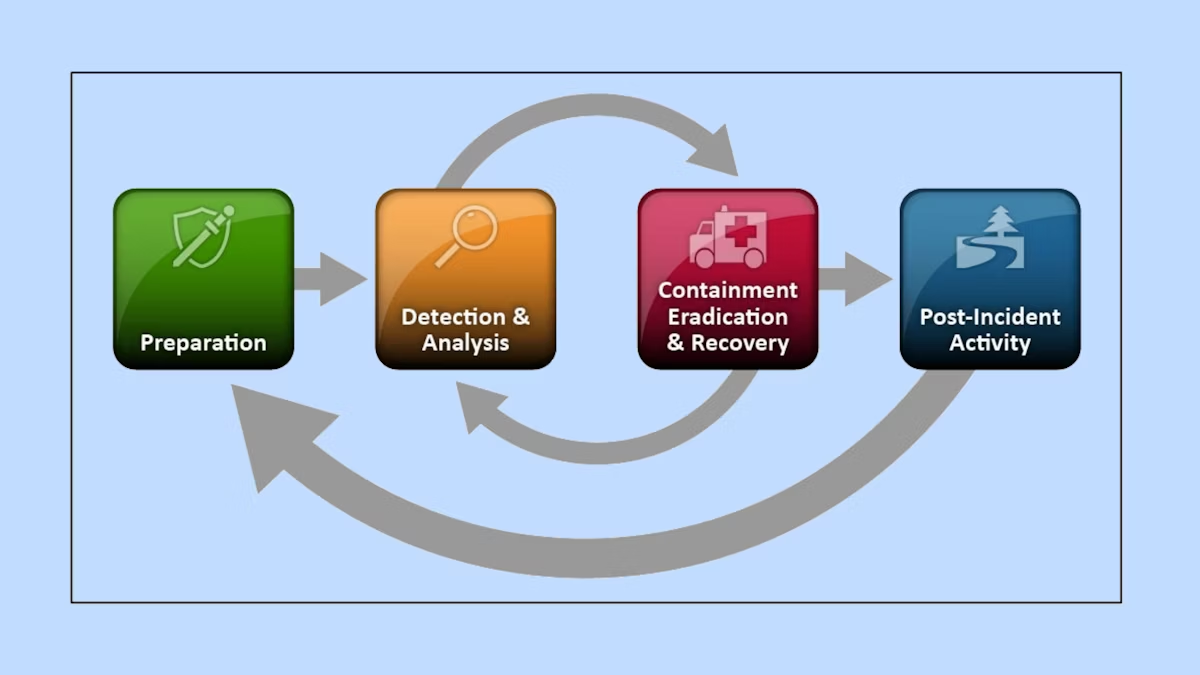
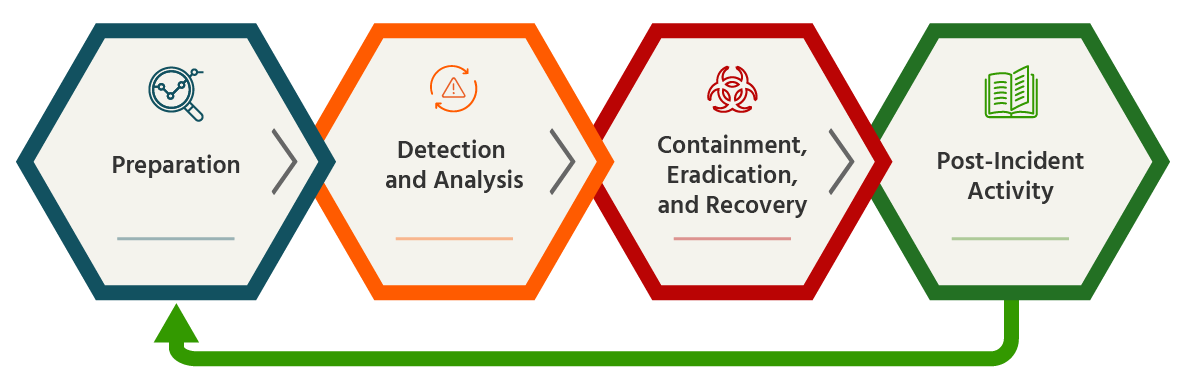
The 7 Phases of Incident Response
Any company must understand the seven steps of incident response. These stages guarantee the effective and systematic management of security events.
1. Preparation
The incident response lifecycle is built upon the preparation phase. In this phase, organizations create rules, tools, and practices to manage potential events.
The necessary preparatory phase steps consist of the following:
- Creating an incident reaction strategy
- Creating an incident response team (IR team)
- Running drills and incident response testing
- Selecting dependable incident response solutions and incident response program
- Giving staff security best practice training
Many incident response companies provide incident response consultancy to enable businesses to create sensible strategies. Dealing with the best incident response companies guarantees intense preparation for you.
2. Identification
The identifying stage focuses primarily on spotting security incidents. The aim is to determine if an occurrence counts as an incident.
Essential tasks in this stage include:
- System monitoring with security incident response software
- Using logs and alerts to spot indications of possible breaches
- Using incident management services to confirm incidents
- Notifying the team in incident response for quick reaction
The correct incident response management software and technologies in place will determine the accuracy of this step.
3. Containment
Containment is the separation of the impacted systems to stop the incident from spreading. Good containment techniques help to significantly lower damage.
Among the steps in the containment phase are:
- Temporary containment is used to isolate impacted systems quickly
- Long-term containment is aimed at reducing hazards while systems are rebuilt
- Conserving evidence for forensic study
Cyber incident response companies frequently use advanced security response services to contain incidents effectively.
4. Eradication
The eradication step targets eradicating the fundamental cause of the breach once the incident is under control. This stage guarantees that the threat is no longer present.
Among the essential eradication tasks are:
- Deleting dangerous files or software
- Fixing holes exploited during the actual incident
- Doing extensive scans under cyber incident response services
Dealing with qualified incident response service providers guarantees complete and successful eradication.
5. Recovery
The recovery phase involves restoring systems to regular operation while guaranteeing their security. This stage needs close observation to prevent reinfection.
Among the recovery tasks are:
- Data restoration from backups
- Systems of testing security and functionality
- Tracking systems for indications of residual hazards
- Confirming that business activities are returning to normal
Specialized incident management consultancy provided by incident response companies helps with safe recovery procedures.
6. Lessons Learned
The lessons learned will help improve the following incident response initiatives. After an incident, the IR team investigates closely to determine what went wrong and how to prevent future ones.
Among the critical tasks in this phase are:
- Post-mortem analysis carried out with the incident response team
- Pointing up flaws in the incident response plan
- Based on results, updating rules and practices
- Using suggested improvements from incident response consultancy
Regular reviews and incident response testing help guarantee the organization's readiness.
7. Transmission of Information (Communication)
Good communication is absolutely essential throughout the incident response lifecycle. Depending on the degree of the breach, companies must notify staff members, customers, and sometimes the public.
Among the essential communication responsibilities are:
- Immediately notifying the impacted parties
- Alerting management of incident developments
- For clear communication, coordinating with incident response service providers
- Keeping openness to safeguard the name of the company
Key Benefits of Implementing an Incident Response Lifecycle
Investing in a disciplined incident response lifecycle has several clear advantages for companies. Whether your company is small or big, having a sound strategy supported by incident response services and incident response software will make a big difference. These are some main advantages:
Reducing Downturn and Damage
Effective incident response management mainly aims to minimize damage and operating downtime. Comprehensive incident response strategies and experienced incident response service providers help to identify, contain, and eradicate incidents quickly. This reduces disturbance and speeds up recovery for your company.
Compliance of Regulations
Different sectors have tight rules about data security and breach reporting. Ignoring these rules could lead to severe penalties and legal actions. Using incident response consulting services guarantees that your incident response procedures satisfy legal standards. Cyber security incident response services enable you to remain GDPR, HIPAA, and CCPA compliant.
Guarding Customer Trust and Reputation
An improperly handled security incident can sour client confidence and harm your business's reputation. Having a trustworthy incident response team and using security response services shows your clients that you prioritize cybersecurity. Clear communication and quick responses help customers and partners feel their data is protected.
Money Saving
A data breach has terrible financial effects. Legal fees, damage management, and lost income-related expenses can all rapidly rise. Good incident management services help you control these expenses by lowering the scope and severity of incidents. Dealing with a significant breach is significantly more expensive than investing in incident response testing and incident response solutions.
Continuous Improvement
Frequent reviews and post-incident analysis help improve your security posture. Your company gains increasing resilience over time through incident response testing and learning from every incident. Working with seasoned cyber incident response companies can offer insightful analysis to help you improve your security.
Common Challenges in Incident Response
Even with a strong incident response plan, organizations may have difficulties during the response. These are many typical problems together with solutions:
Delayed Detection
Incidents delayed in detection might cause significant damage. Investing in advanced incident response software and ongoing monitoring will assist in identifying hazards early on. Cyber security incident response services often offer real-time, 24/7 monitoring to capture incidents.
Lack of Preparedness
Incident response can become chaotic without a clear plan. To create a strong plan and stay prepared, engage in incident management consulting and routine incident response testing.
Insufficient Resources
Some companies lack the resources or knowledge required to manage challenging situations. Under these circumstances, outsourcing to incident response companies or leveraging incident response as a service can supply the necessary resources and expertise.
Poor Communication
Good communication is crucial throughout an incident. Clearly define your channels of contact and ensure that every interested party receives quick information. A communications lead on your IR team can handle this efficiently.
Why Choose Professional Incident Response Services?
Managing security events calls on expertise, resources, and experience. Working with the best incident response firms offers various benefits:
- Expertise: Experience in incident response companies brings specific understanding.
- Speed: Early reaction from cyber security incident response services reduces harm.
- Tools: Advanced incident response management software helps to handle it effectively.
- Compliance: Incident response consultancy helps satisfy legal criteria.
- Peace of Mind: Knowing that experts are handling situations helps one to have peace of mind and lowers stress.
Working with professionals guarantees that your company stays safe whether you need an incident response as a service, incident response solutions, or IR cyber security help.
Protect Your Company with Gini
Are you ready for your company to manage online risks? Do not wait until too late. To protect your information and reputation, Gini provides industry-leading incident response services. Ensure your company remains safe by contacting our knowledgeable event response team.